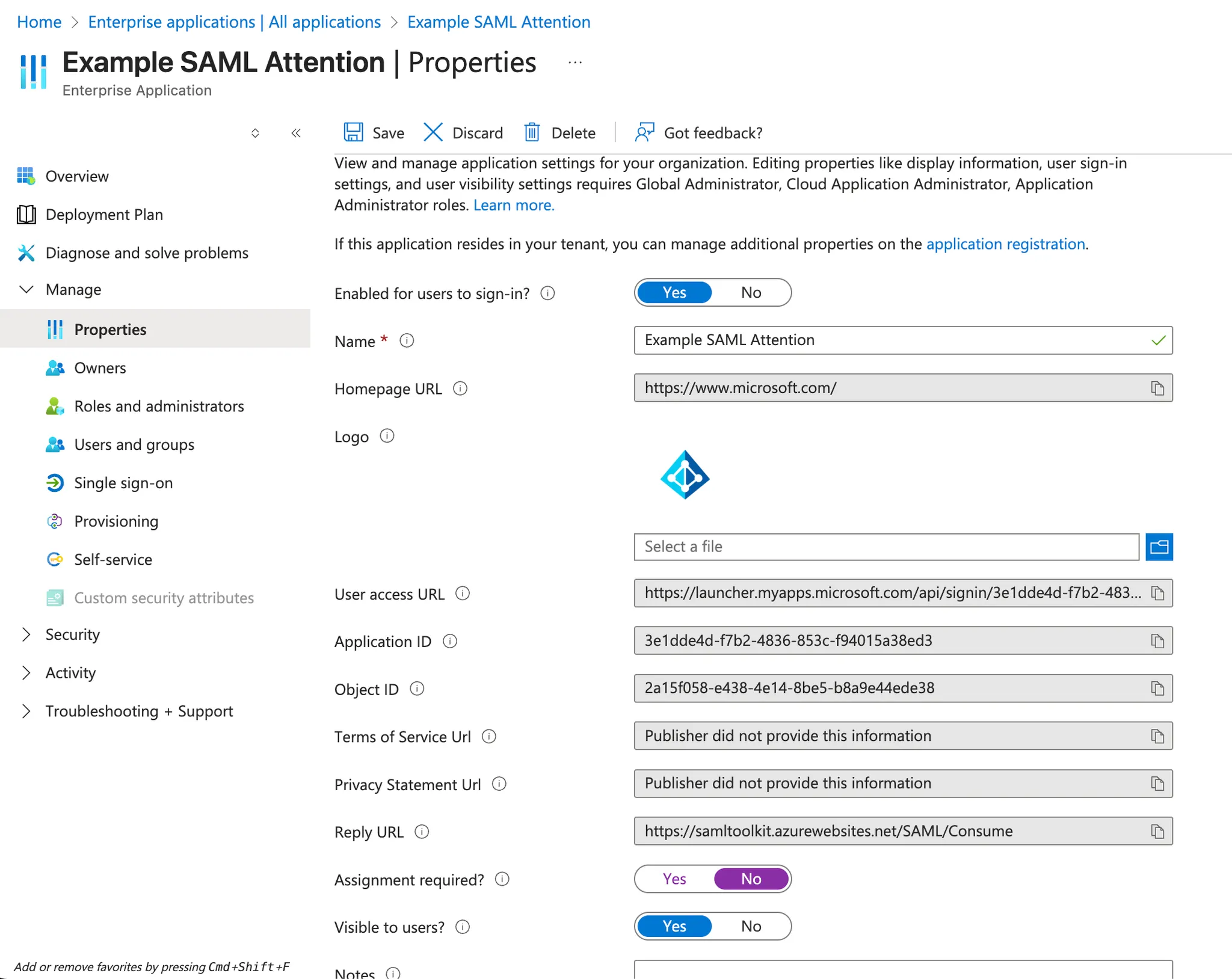
Google SSO Setup
- Go to the Google Cloud Platform and choose your project: https://console.cloud.google.com/apis/credentials
- Click on
+ Create Credentialsand chooseOAuth client ID - Choose
Web applicationas application type and give a name. - Under
Authorized Redirect URIs, paste the following URI:
- After saving, a Client ID and Client Secret will be generated. Provide these to your Attention point of contact to finalize setup.
- After doing this, the Attention team will follow up with the URL your team needs to use log in with Google OAuth. This URL will take you directly to your Google account login. Once you log in successfully, you will be redirected automatically to the Attention paltform homepage.
NOTE: The authentication mechanism does not auto provision users on Attention. Users must be invited to Attention before trying to authenticate via Google.
Okta SSO Setup
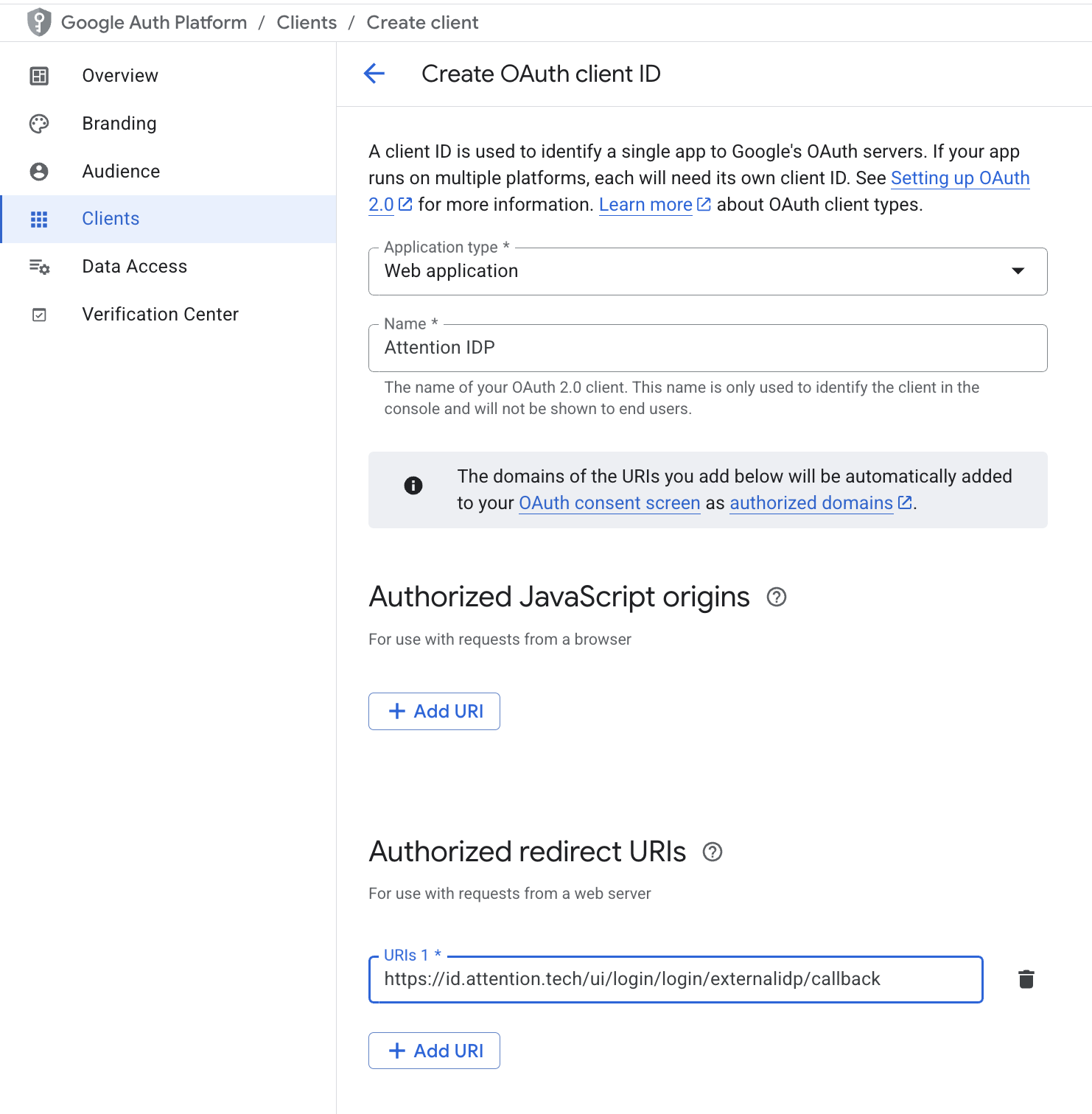
- As an Okta administrator, log into the administration panel and navigate to the list of applications.
- Once there, click to create a new App Integration, and choose
OIDC - OpenID Connect. - Choose
Web Applicationas the application type.
- Give it an identifiable name (this is for your own purposes to easily identify it among other applications you might have configured).
- In the
Sign-in redirect URIspaste the identity service redirect URL which is the following one: https://id.attention.tech/ui/login/login/externalidp/callback - Once saved, provide the Client ID, Secret and Issuer URL (which will look something like: https://trial-1925566.okta.com) to your point of contact at Attention. Your Attention point of contact will then notify you once the configuration has been completed.
- Once the Web Application has been created, add your team members to organization and/or group in Okta that is configured to use this new application.
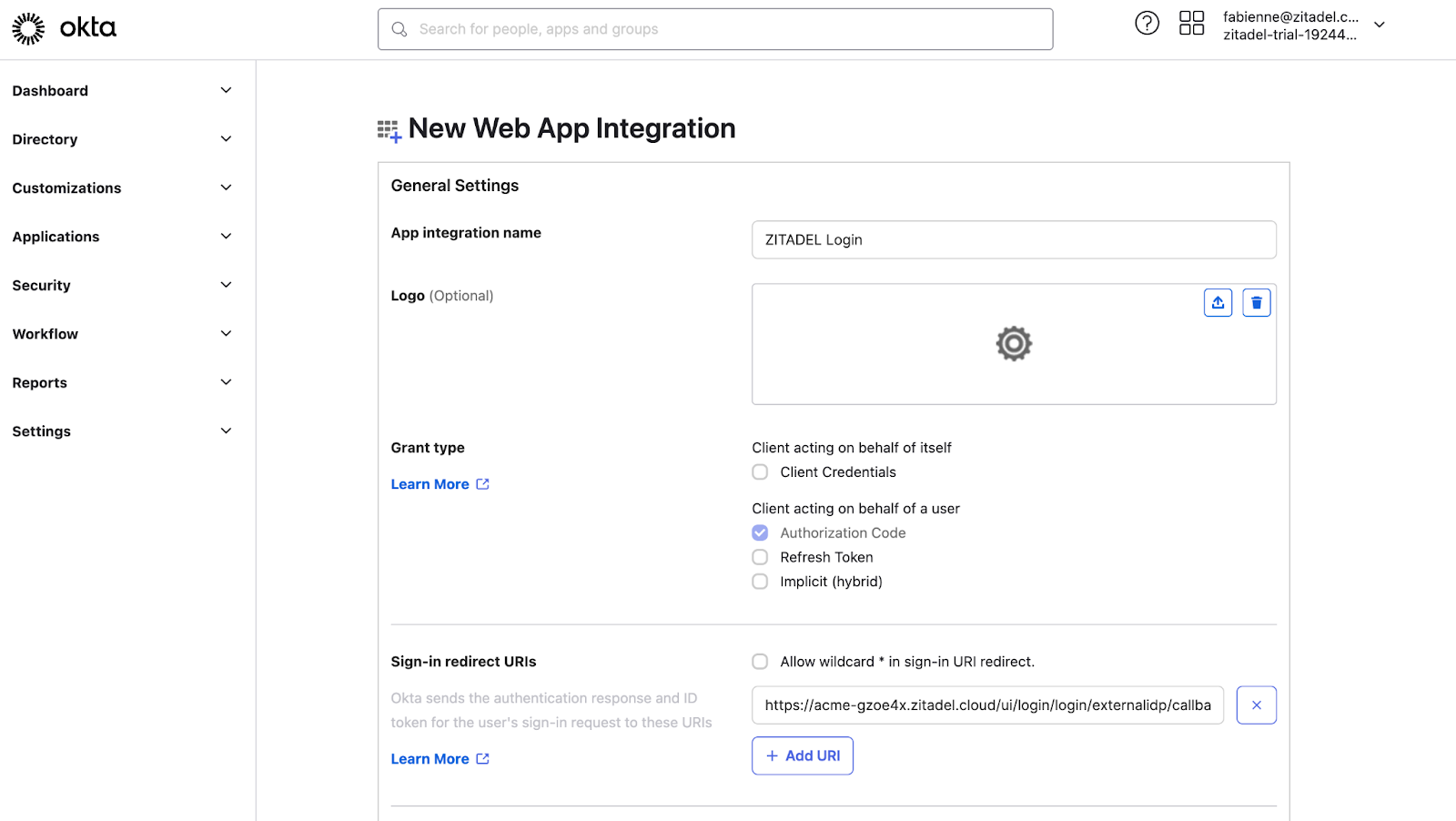
EntraID SAML Setup
Register a new enterprise application in EntraID- Navigate to the Enterprise App registration menu.
- Search for “SAML Toolkit” and click on the
Microsoft Entra SAML Toolkitcard. - Change the name if desired and click “Create”
- This will create an application that will be configured in the subsequent steps.

Configure SAML
-
Click on the Application and Go to
Manage>Single sign-on -
Select SAML
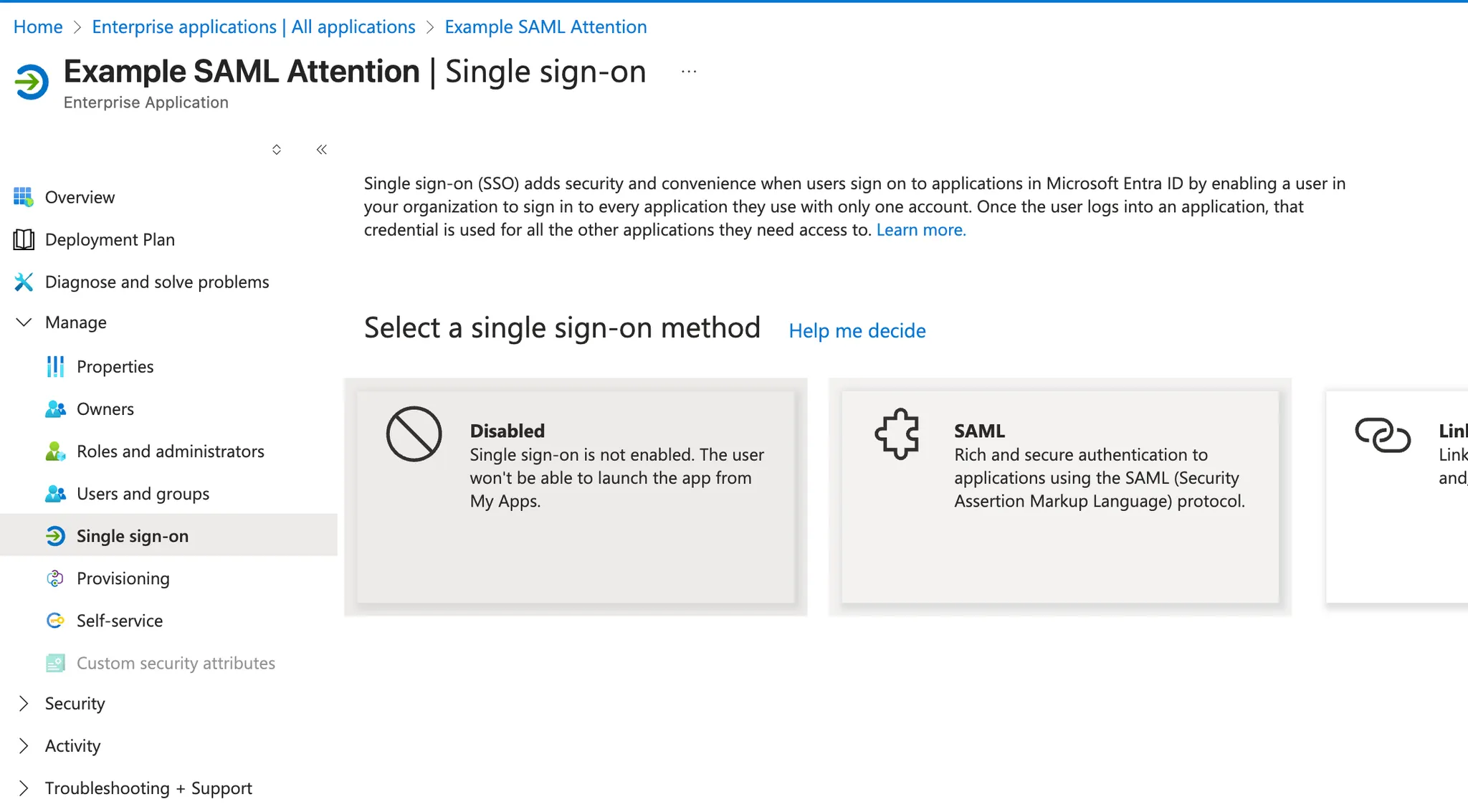
-
Once redirected to the Single Sign-On details, copy the URL from
SAML Certificates>App Federation Metadata URLto your clipboard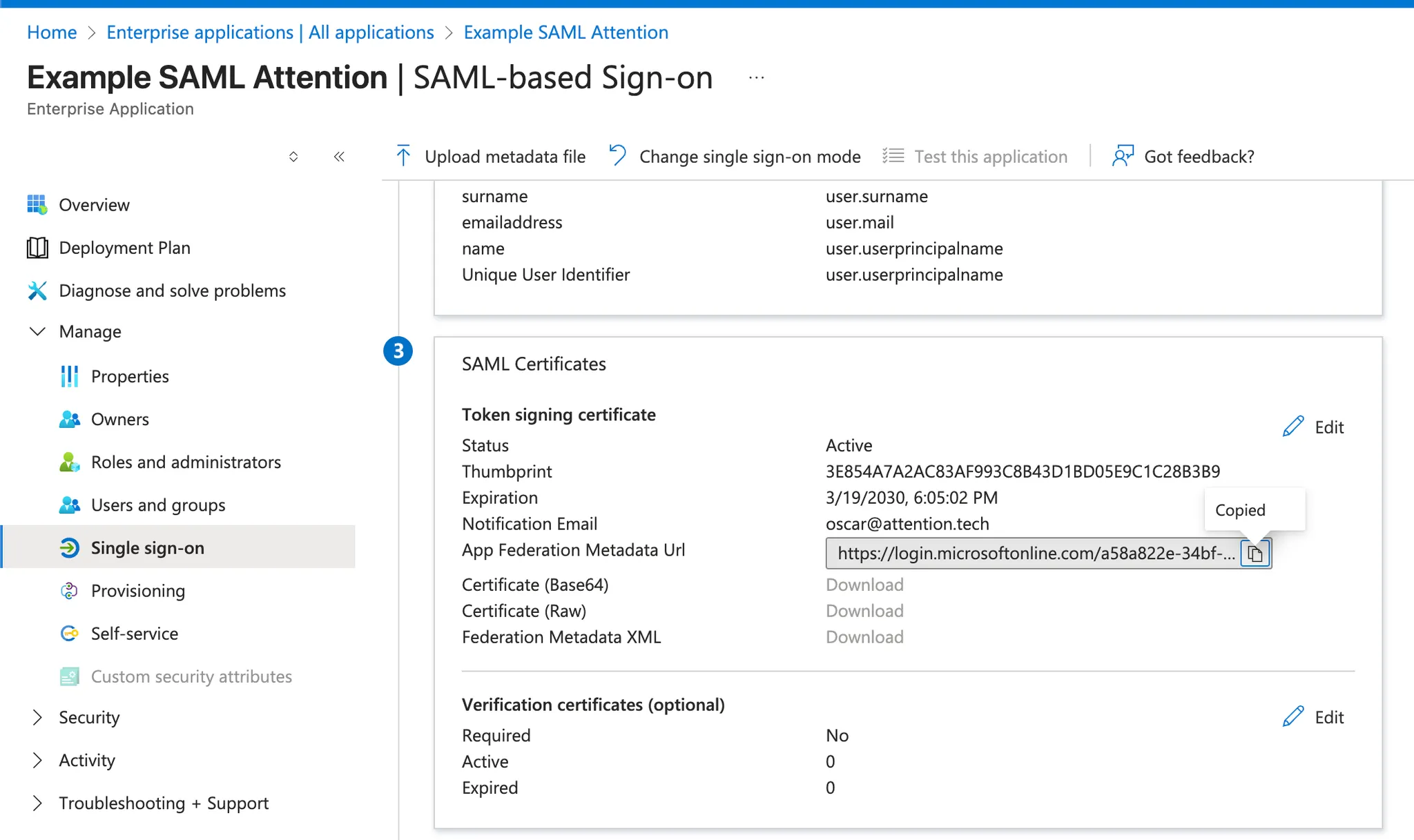
- Provide this URL to your point of contact at Attention.
- The Attention team will then provide a series of URLs like the following:
Entity ID URL: https://id.attention.tech/idps/00000000000000000000/saml/metadata Reply URL: https://id.attention.tech/ui/login/login/externalidp/saml/acs
Sign On URL: https://id.attention.tech/ui/login/login/externalidp/saml/acs
Logout URL: https://id.attention.tech/idps/00000000000000000000/saml/slo
- Return to the
Single sign-Onsettings of your application and click Edit onBasic SAML Configuration

-
Paste in the URLs provided by the Attention team to each matching field. Leave
Relay State URLempty.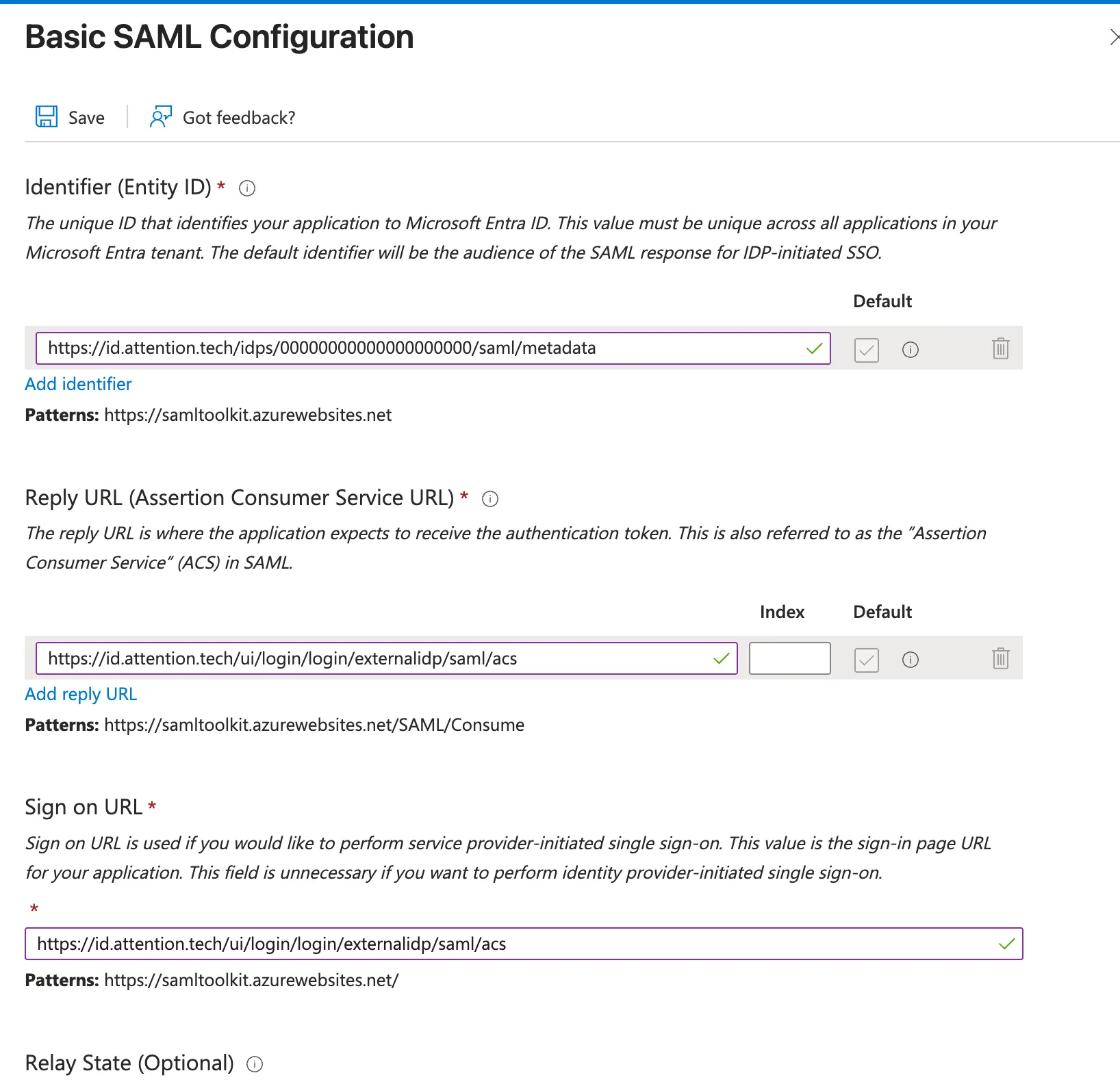
-
Save changes and confirm your
Basic SAML Configurationsection now looks like this:
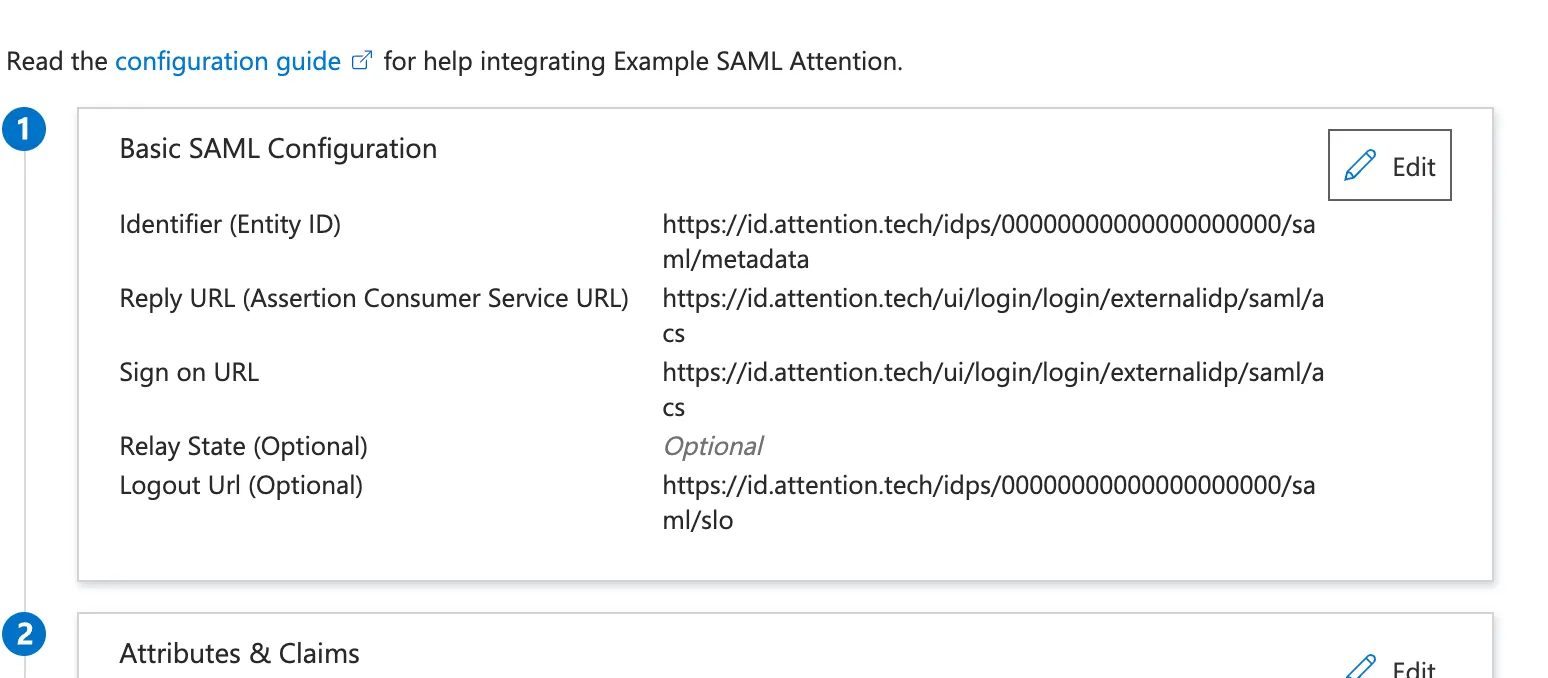
- Once completed, notify your Attention point of contact.
- The Attention team will follow up provide the URL needed to log in using EntraID. This URL will take you directly to your EntraID login. Once users login, they will be redirected to the Attention homepage.
NOTE: The authentication mechanism does not auto-provision users on Attention. Users must be invited to Attention before trying to authenticate via EntraID.
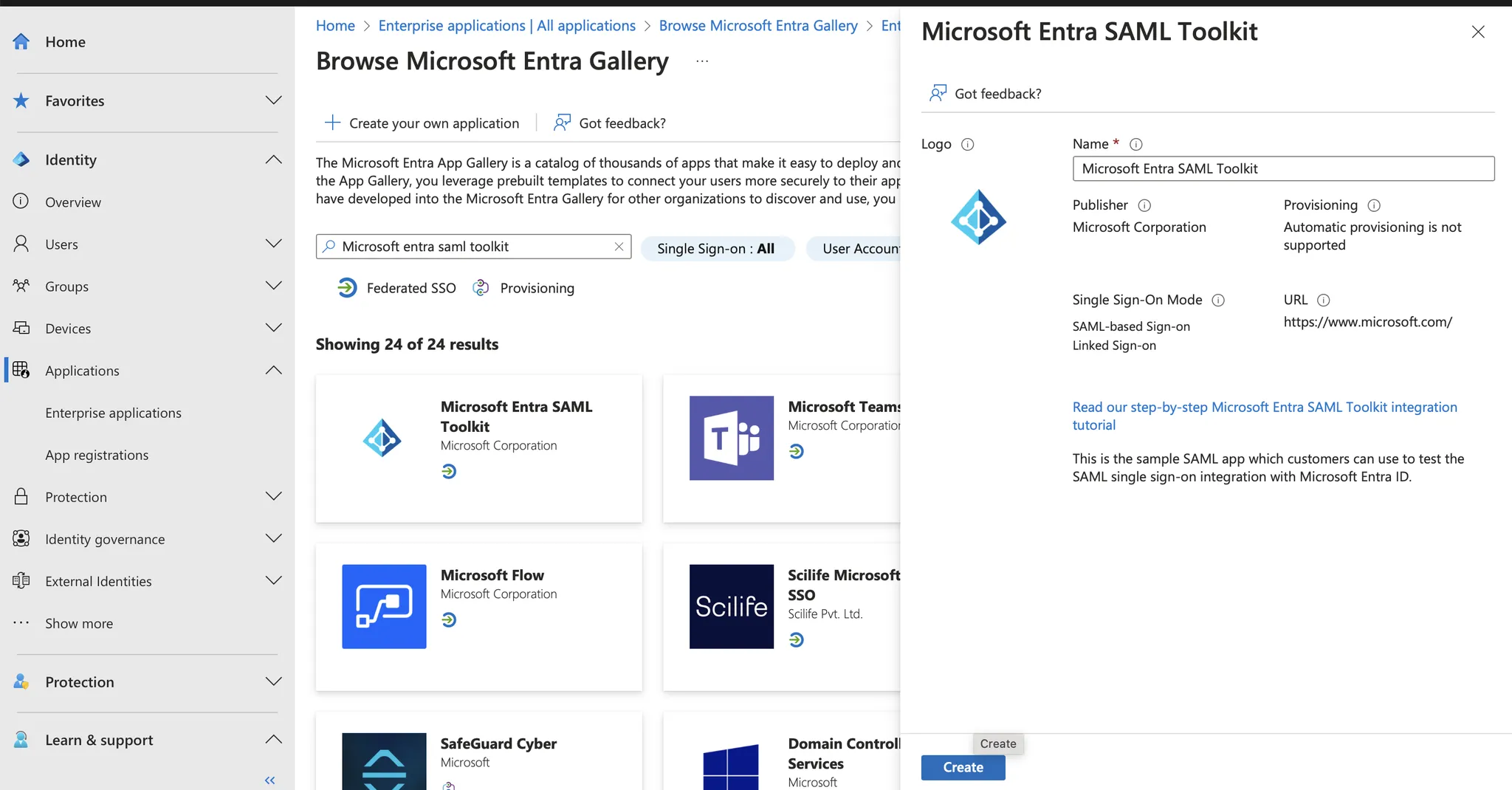
Configure User Requirements for App Access
There are 2 options for requiring Attention users to authenticate via EntraID. Option 1: Assign users and groups manually via the settings inManage > Users and groups
**Option 2: **Require all Attention users to authenticate by default. To do this, naviagate to
Manage > Properties and set Assignment required? to “No”